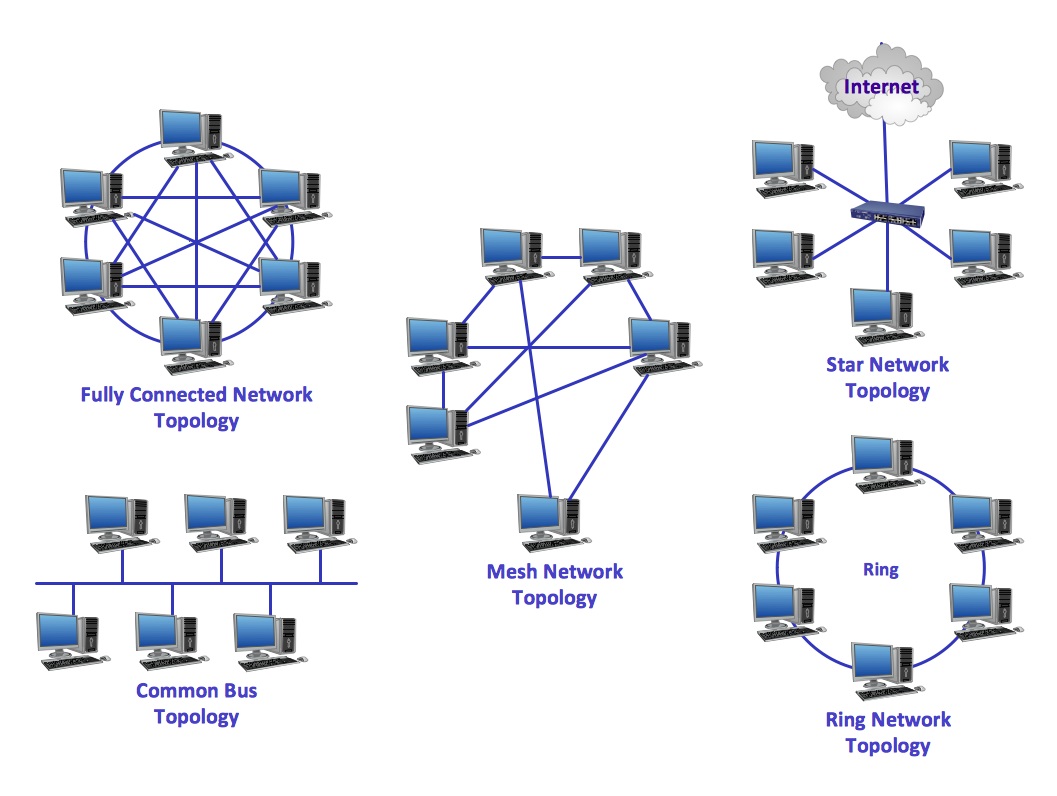
Peer-to-peer:
- All connected computers have equal status- there is no centralised management
- Can all share files and peripherals
- Each peer computer may be accessed by any other peer
- Prone to data collisions…
- Really good to share files and work together on projects
- Network speed is reduced
- Often implemented over the internet
- Used to facilitate file-sharing (both legal and illegal) and BitCoin payments.
Client server:
- Most common architecture
- Dedicated, high-spec machine is the Server:
- centralised storage of data
- processing of shared files
- printing
- internet access etc
- Security
- Clients request services from the Servers.
- File server, web server, print server etc
- Data Centres = multiple servers stacked together
- Virtualised servers:#
- efficiency ++
- energy consumption --
- The types of servers:
- File
- Database
- Website
The 7 layer OSI Model:
- OSI ( Open System Interconnection
- Lots of different networks, OS & protocols
- No standard means of communication / sharing data between different type devices
- OSI model evolved to create a standard
- Describes a set of protocols that allow computers with different architectures to be linked together so that they can communicate & share data
The 7 stages:
Seven Layers of OSI Model:
• Application Layer - Network aware applications. It is the software that the user interacts with.examples of this are email, web browsers, print servers, network drives and social media
• Application Layer - Network aware applications. It is the software that the user interacts with.examples of this are email, web browsers, print servers, network drives and social media
• Presentation Layer -Converts data between formats required for applications & transmission over network. It is responsible for encryption, compression and translation where necessary.
• Session Layer-Converts data between formats required for applications & transmission over network. Examples of this are managing connection sessions, login rights, File/Folder Permissions and access rights.
• Transport Layer-Send the data from the source address to the destination address, it Guarantees end-to-end delivery of data. Handles error checking and correct transmission of sent / received data:
-Check that destination address exists
-Make sure it’s in the correct order
A data packet broken down into sections:
Sequence number =data is in the correct order
FLAGS=
Source port= the IP address of where the data is coming from
Destination port= The IP address of where the data is going
Checksum= To check the data is correct
DATA= the actual data itself
A data packet's journey can be viewed using traceroute
Destination port= The IP address of where the data is going
Checksum= To check the data is correct
DATA= the actual data itself
A data packet's journey can be viewed using traceroute
• Network Layer- Responsible for transmitting and routing data packets via the shortest possible path across the network to their destination (shortest time not distance!).
• Data Link Layer- Decides whose turn it is to send / receive data (“Bus arbitration”). Finds the physical device on the network generally a switch.
• Physical Layer- This holds the Physical properties of the network examples are:
-Cables
-Voltages & Frequencies
-Bit encoding
-Transfer rates
TCP/IP:
- Transmission control protocol/internet protocol
- A suite of protocols
- Describe how data is communicated over a network.
There are 4 layers:
Application
Transport
Internet
Link (Network Access / Network Interface)
PDU:
- Protocol Data unit
- Term used to describe the information on any given layer of the TCP/IP stack
- Each layer has an associated PDU:
- Application layer ; DATA
- Transport layer; SEGMENT (TCP) DATAGRAM (UDP)
- Internet layer: DATAGRAM
- Network Access layer: FRAME (data link layer) Bits (Physical layer)
- Terminology is not strictly followed… often the term ‘packet’ is used at any layer!
Layer addressing:
Each layer has its own method of identifying the source address & destination address of dataAt the application layer there is just data, no addressing. At the transport layer data is broken into segments that use ports to identify services. At the Internet layer each network device has a unique IP address. IP datagrams use IP addresses to reach the correct destination. IPv4 - 192.168.0.1. (4 8 bit values)IPv6 is implemented to give a wider range of IP addresses.
At the link layer Ethernet splits data packets into frames. Frames use the physical address of the device
the MAC address - uses 6 x 2 digit hex values: 88-CB-87-E4-17-4F.
MAC address can never be changed and it is unique to a device
MAC (Medium Access Control) Address
Physical Layer
- Devices that extend the physical network
- Help relay bits from A to B
- Devices examine data packets and make decisions based on IP address of sender / recipient
- Devices examine segments and make decisions based on Port number
Datagram:
- Self-contained / self-sufficient unit of data
- Contains source & destination addresses in the header
- Primarily used in wireless communications
- Data sent to destination without any pre-defined route
- No guarantee of delivery
- No confirmation upon successful delivery
- Order of sending / receiving datagrams is not considered
- Supports a maximum of 65,535 bytes at a time